Navigating The Cybersecurity Landscape: A Comprehensive Guide To Nessus Vulnerability Scanning
Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning
Related Articles: Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning
- 2 Introduction
- 3 Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning
- 3.1 Understanding the Essence of Nessus Map
- 3.2 Benefits of Utilizing the Nessus Map
- 3.3 Implementing Nessus Map for Optimal Security
- 3.4 Addressing Common FAQs about Nessus Map
- 3.5 Tips for Optimizing Nessus Map Usage
- 3.6 Conclusion: Empowering Cybersecurity with Nessus Map
- 4 Closure
Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning
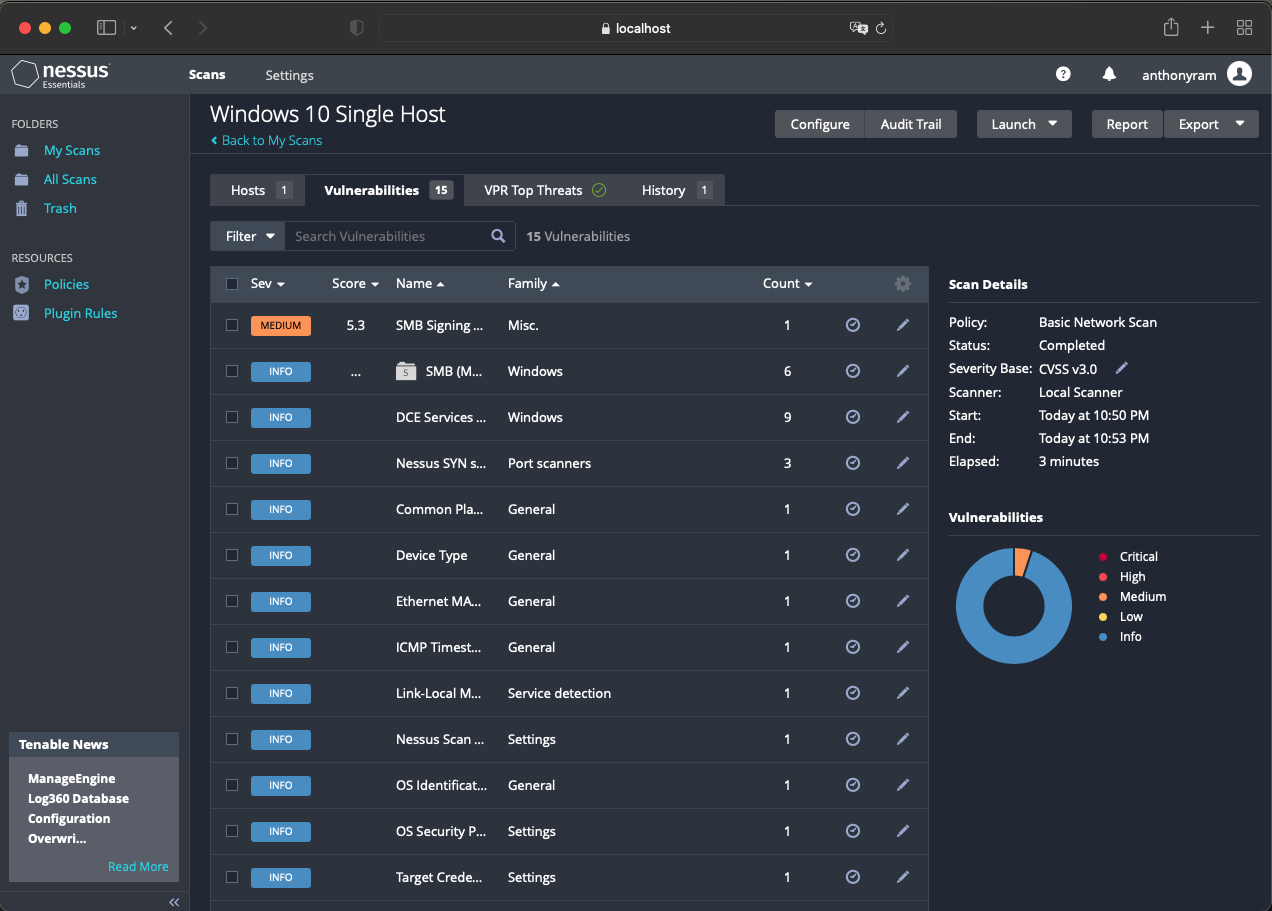
In the ever-evolving world of cybersecurity, vulnerability scanning plays a crucial role in identifying and mitigating potential threats. One of the leading tools in this domain is Nessus, a comprehensive vulnerability scanner developed by Tenable. While Nessus itself is a powerful platform, its effectiveness is significantly enhanced by the Nessus Map, a powerful visualization tool that allows security professionals to gain valuable insights into their network’s security posture.
This guide delves into the world of Nessus Map, exploring its functionalities, benefits, and how it can be leveraged to bolster an organization’s cybersecurity strategy.
Understanding the Essence of Nessus Map
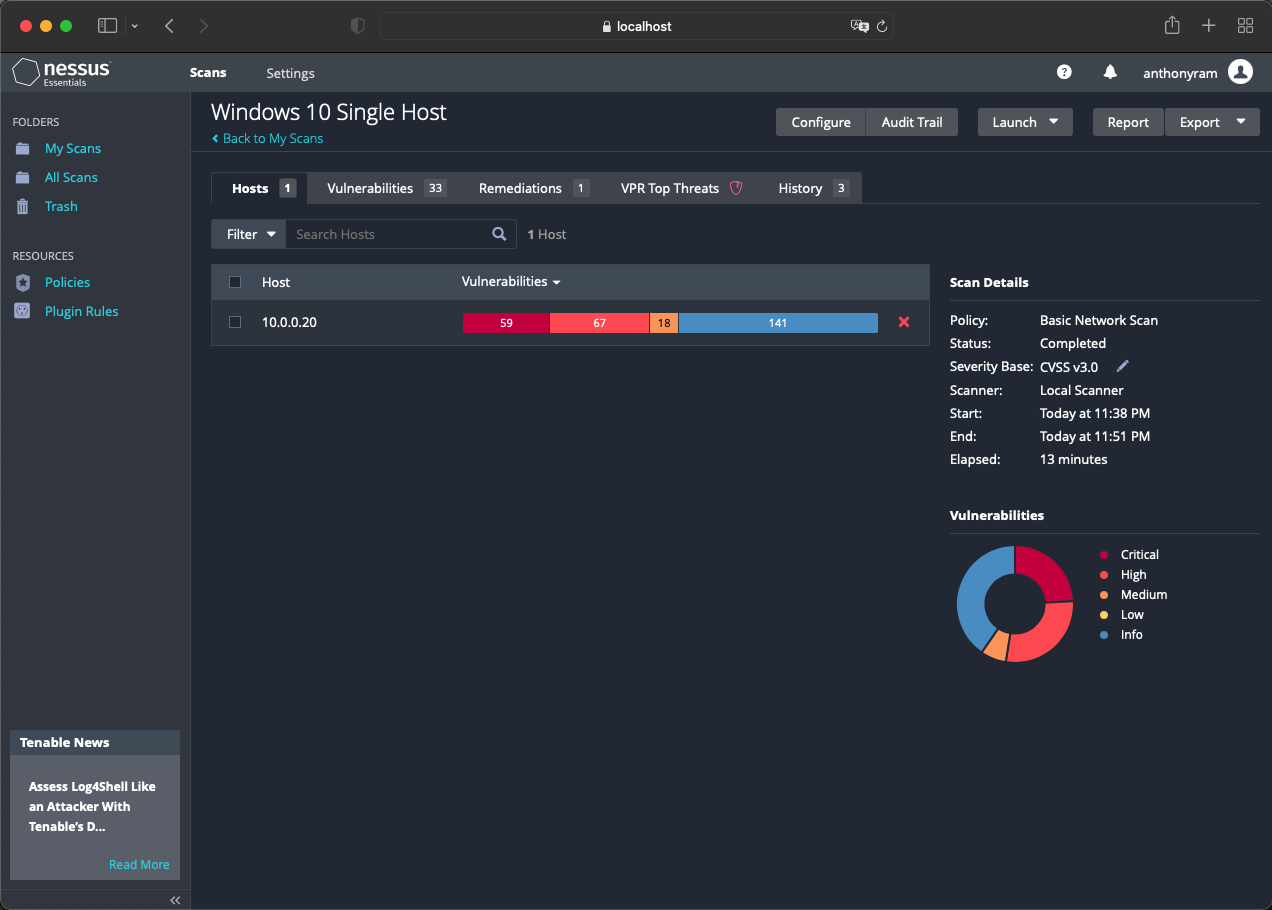
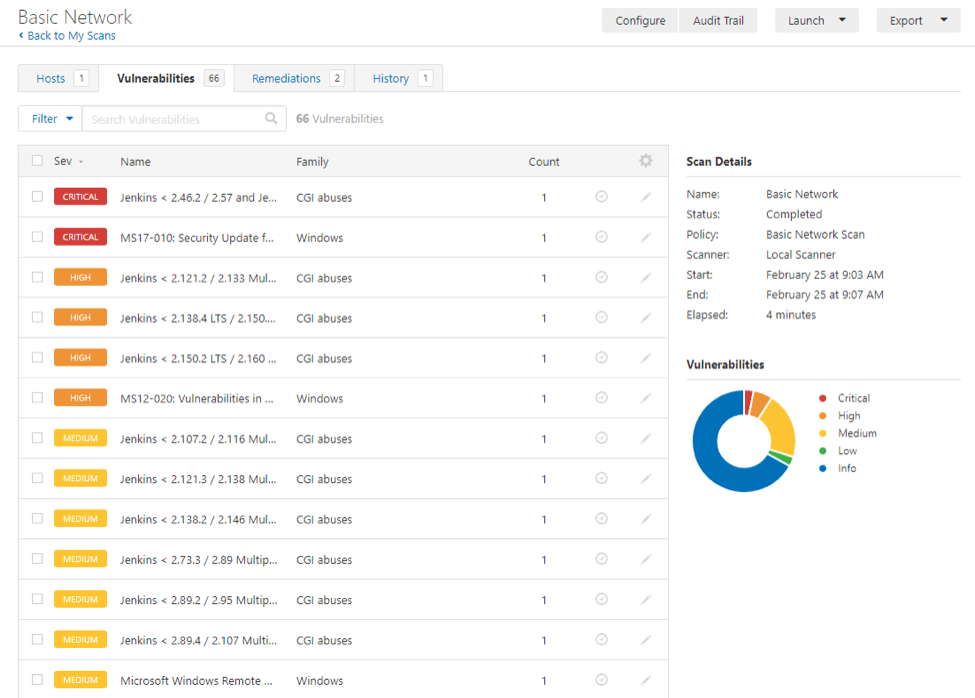
The Nessus Map is a dynamic, interactive visualization tool that provides a clear, graphical representation of an organization’s network infrastructure, highlighting vulnerabilities and security risks. It goes beyond simply presenting a list of vulnerabilities, offering a holistic view of the security landscape.
Key Features of Nessus Map:
- Network Topology Visualization: The Nessus Map provides a visual representation of the network, showcasing the interconnectedness of devices, systems, and applications. This visual understanding allows security professionals to identify potential attack paths and understand the flow of data within the network.
- Vulnerability Heatmap: The map employs a color-coded system to represent the severity of vulnerabilities. This allows for quick identification of high-risk assets and vulnerabilities that require immediate attention.
- Detailed Asset Information: Each asset on the map is linked to detailed information about its configuration, operating system, installed software, and detected vulnerabilities. This granular level of detail enables security professionals to understand the specific vulnerabilities affecting each asset and prioritize remediation efforts.
- Real-time Updates: The Nessus Map dynamically updates in real time, reflecting the latest scan results and any changes in the network environment. This ensures that security professionals have access to the most current information, enabling them to respond swiftly to emerging threats.
- Customizable Views: Users can customize the Nessus Map to suit their specific needs. This includes filtering assets by specific criteria, focusing on particular vulnerabilities, or creating custom views to highlight specific areas of concern.
- Integration with Other Tools: The Nessus Map seamlessly integrates with other Tenable products, such as Nessus Professional and Tenable.io. This integration allows for comprehensive vulnerability management and reporting, enabling security teams to track remediation progress and ensure ongoing security.
Benefits of Utilizing the Nessus Map
The Nessus Map offers numerous benefits to organizations seeking to enhance their cybersecurity posture. These benefits can be summarized as follows:
- Improved Vulnerability Prioritization: By visually highlighting vulnerabilities based on their severity, the Nessus Map helps security professionals prioritize their remediation efforts. This ensures that the most critical vulnerabilities are addressed first, minimizing the risk of exploitation.
- Enhanced Threat Visibility: The map provides a clear understanding of the organization’s network infrastructure and its vulnerabilities, offering a comprehensive view of potential attack vectors. This enhanced visibility allows security teams to proactively identify and address potential security risks.
- Simplified Security Reporting: The Nessus Map simplifies the process of generating security reports. Users can easily create reports that showcase the network’s security posture, highlighting key vulnerabilities and remediation progress. This simplifies communication with stakeholders and facilitates informed decision-making.
- Improved Collaboration: The Nessus Map can be shared with other members of the security team, enabling collaboration on vulnerability remediation. This fosters a shared understanding of the organization’s security posture and facilitates effective teamwork.
- Faster Remediation: The Nessus Map helps expedite the vulnerability remediation process by providing clear guidance on which assets to focus on and the specific vulnerabilities to address. This streamlined approach reduces the time it takes to patch vulnerabilities and improve the organization’s overall security.
- Reduced Risk of Breaches: By proactively identifying and mitigating vulnerabilities, the Nessus Map helps organizations reduce the risk of security breaches. This is crucial in today’s threat landscape, where cyberattacks are becoming increasingly sophisticated and targeted.
Implementing Nessus Map for Optimal Security
To effectively leverage the power of the Nessus Map, organizations need to implement it strategically and ensure its integration with their existing security processes.
Steps for Effective Implementation:
- Define Security Objectives: Clearly define the organization’s security objectives and how the Nessus Map can contribute to achieving them. This provides a framework for utilizing the map effectively.
- Configure Nessus Scanning: Ensure that Nessus is configured to scan the entire network and identify vulnerabilities comprehensively. This provides the necessary data for the Nessus Map to function effectively.
- Customize the Map: Tailor the Nessus Map to suit the organization’s specific needs and priorities. This may involve filtering assets, highlighting specific vulnerabilities, or creating custom views.
- Integrate with Existing Tools: Integrate the Nessus Map with other security tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and vulnerability management platforms. This creates a comprehensive security ecosystem.
- Regularly Review and Update: Regularly review the Nessus Map and update it with the latest scan results. This ensures that the map remains relevant and provides an accurate reflection of the organization’s security posture.
- Train Security Teams: Provide training to security teams on how to effectively utilize the Nessus Map and interpret its data. This ensures that the tool is leveraged effectively to enhance the organization’s security posture.
Addressing Common FAQs about Nessus Map
Q1: What is the difference between Nessus and Nessus Map?
A: Nessus is a vulnerability scanner, while Nessus Map is a visualization tool that provides a graphical representation of the scan results. Nessus identifies vulnerabilities, while Nessus Map helps security professionals understand and prioritize these vulnerabilities within the context of the network infrastructure.
Q2: Can Nessus Map be used for external vulnerability scanning?
A: While the Nessus Map primarily focuses on visualizing internal network vulnerabilities, it can also be used for external vulnerability scanning. However, it may require additional configuration and integration with external scanning tools.
Q3: Is the Nessus Map available for free?
A: The Nessus Map is a feature of the Nessus Professional and Tenable.io platforms, which are not free. However, Tenable offers a free version of Nessus, which includes basic vulnerability scanning capabilities.
Q4: How often should I update the Nessus Map?
A: The frequency of updates depends on the organization’s specific needs and the dynamism of the network environment. Ideally, the map should be updated regularly, at least once a week, to reflect the latest vulnerability information and any changes in the network infrastructure.
Q5: Can I customize the Nessus Map to focus on specific vulnerabilities?
A: Yes, the Nessus Map is highly customizable. Users can filter assets, highlight specific vulnerabilities, and create custom views to focus on areas of particular concern.
Tips for Optimizing Nessus Map Usage
- Start with a Comprehensive Scan: Ensure that Nessus scans the entire network thoroughly to capture all vulnerabilities.
- Prioritize High-Severity Vulnerabilities: Focus on vulnerabilities classified as high or critical severity, as these pose the most immediate risk.
- Use Filtering and Custom Views: Leverage filtering and custom views to create focused views of the map that highlight specific vulnerabilities or assets.
- Integrate with Other Security Tools: Combine the Nessus Map with other security tools to create a comprehensive security ecosystem.
- Regularly Review and Update: Make reviewing and updating the map a regular part of your security routine.
Conclusion: Empowering Cybersecurity with Nessus Map
The Nessus Map is a powerful tool that empowers organizations to visualize their network security posture, identify vulnerabilities, and prioritize remediation efforts. By providing a clear, graphical representation of the security landscape, the Nessus Map facilitates informed decision-making, enhances threat visibility, and ultimately strengthens an organization’s cybersecurity defenses. In today’s ever-evolving threat landscape, the Nessus Map is an invaluable asset for any organization seeking to protect its critical assets and maintain a strong security posture.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Cybersecurity Landscape: A Comprehensive Guide to Nessus Vulnerability Scanning. We hope you find this article informative and beneficial. See you in our next article!
You may also like
Recent Posts
- Beyond Distortion: Exploring The World With Non-Mercator Projections
- Navigating The Natural Beauty Of Blydenburgh Park: A Comprehensive Guide To Its Trails
- Navigating The Wilderness: A Comprehensive Guide To Brady Mountain Campground Maps
- Navigating The Road Less Traveled: A Comprehensive Guide To Gas Map Calculators
- Navigating Bangkok: A Comprehensive Guide To The BTS Skytrain
- Navigating Copenhagen: A Comprehensive Guide To The City’s Train Network
- Unlocking The Secrets Of The Wild West: A Comprehensive Guide To Red Dead Redemption 2’s Arrowhead Locations
- Unveiling The Enchanting Tapestry Of Brittany: A Geographical Exploration
Leave a Reply